Website Hacks & Security: A Reality Check
After the vulnerability in Themepunch’s Revolution Slider was made public in the fall of 2014, it became dreadfully obvious how vulnerable websites really are: The plugin’s extreme popularity with site owners, web designers and theme developers made it incredibly easy (for almost everybody) to attack, exploit and infect a site via the security hole contained within the plugin’s code.
One of the reasons they still don’t know it is the fact that their Revolution Slider came packaged with a theme, buried somewhere in the theme’s directory.
I Installed The Update So I’m No Longer In Danger, Right?
Wrong.
Unless you’re keeping up with everything that’s going on in the exploit world, are monitoring your log files, log in attempts and everything around it (and even IF you do!) you are never safe.
Think of it this way: Even if you are the safest driver in the world, you can still get into an accident.
Maybe you’ve heard about the security issue that involved another popular plugin, Yoast’s WordPress SEO, earlier this year. Maybe you even heard about WordPress’ core security issues around the same time – but since then? Anything? No? That’s a good thing, right?
You might want to check the WPScan WordPress Vulnerability Database or the Exploit Database and you will find out that it’s been everything but quiet on the cybersecurity front.
New flaws are being discovered (almost) on a daily basis.
And we’re not even counting successful intrusion attempts due to weak passwords, unsafe handling of login credentials or – the most interesting part – pirated software already containing backdoors.
Data Visualization: Real Log Files, Real Numbers
Below is a table of login attempts to one of our websites – the data is for June 2015 only:
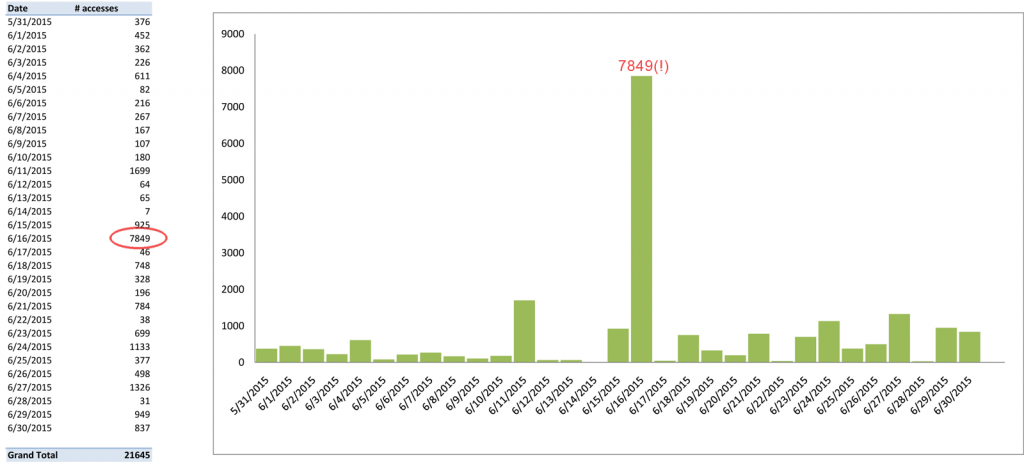
“Protecting” wp-login.php via .htaccess (or other procedures) has no impact on the data, as the requests are still being logged on the server (they only get greeted with a 404, 403 or some other response code).
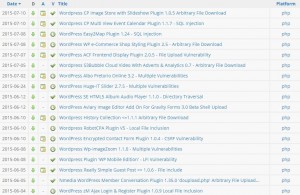
The table below shows the amount of tries to access (read or download) wp-config.php over the period of 15 months (March 2014 – June 2015 – only showing days with 10 or more accesses) – just in case you thought this was over:
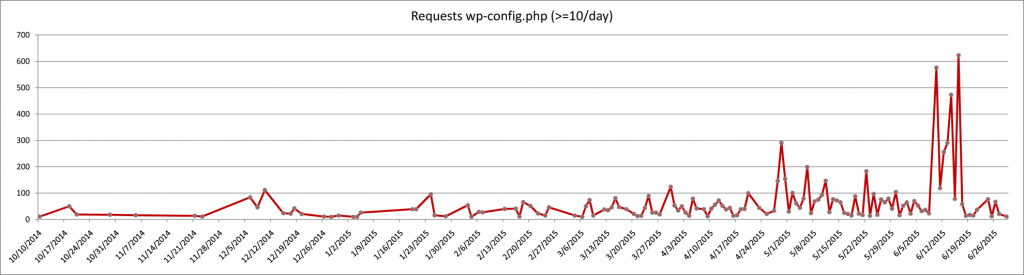
Thousands of IP addresses generated tens of thousands of requests on this one website only.
Blocking the IP addresses is useless, as theses requests most likely come from infected websites that have no clue of what’s going on.
While in the beginning these scans were almost exclusively looking for the above mentioned Revolution Slider exploit, they have evolved and are now looking for known paths in all the plugins and themes containing vulnerabilities listed in the exploit databases or on various other websites.
What They Are Looking For
Besides attacks looking for weak passwords (brute-force attacks) these scans are generally looking for 3 types of vulnerabilities:
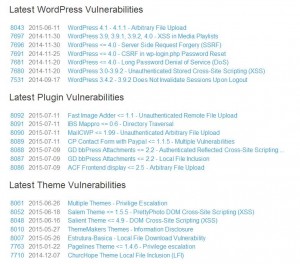
– Directory Traversal (Arbitrary File Access) Exploits: Content of desired file is displayed
Read-only access to (configuration) files like wp-config.php (which contains database credentials, etc)
– Local File Inclusion (LFI) Exploits: Content of file is executed (with the same permissions as the host script/file)
Malicious files can be included and their code is executed
– Arbitrary File Upload Exploits: File can be uploaded, accesses and executed
No sanitation and/or check for the file content is being done which allows any kind of file/code to be uploaded and executed.
How It Got So Bad So Quickly
WordPress’ meteoric rise to the top of the world’s most-used development platforms doesn’t come without growing pains.
It’s a fantastic and very powerful system, but with great power always comes great responsibility.
 It started gaining popularity within the web design community as it was moving from being a blogging CMS only to becoming a robust, complete and easy-to-deploy web development framework; and all of sudden designers who never wrote or saw a single line of code are able to click together interactive websites in no time.
It started gaining popularity within the web design community as it was moving from being a blogging CMS only to becoming a robust, complete and easy-to-deploy web development framework; and all of sudden designers who never wrote or saw a single line of code are able to click together interactive websites in no time.
All they have to do now is select a theme, buy it for very little money (or download the pirated version from some obscure website for free), and – poof – the shiny, new website is done, including forms and maps and sliders and all the other elements they previously had to outsource to programmers.
Need additional functionality? There’s a plugin for that, too.
I know web designers who will try any and all themes and plugins promising a certain functionality; downloading, installing, re-installing, activating, de-activating as many as 10 or 15 at a time. ALL on live production servers.

Have they checked to see if any of them might be listed in the Exploit Database? If it contains known vulnerabilities?
But of course not.
The website is done, the client has paid, and that’s usually the end of it.
Nobody wants to think about the future, what might happen 6 months from now. And the project gets forgotten – who has time to keep track of or think about that one theme they used 2 years ago on that one client’s website?
And that’s how these old, outdated and vulnerable plugins, themes and installations with their gaping security holes remain on servers, ready to be exploited, and ready to infect more websites.
I don’t know a single web designer who keeps track of:
– The WordPress version they used/installed
– The theme’s name, developer, version, etc
– A list of plugins and their versions
But I also don’t know a single client who has ever asked for it.
(How To) Protect Your Investment
Start by seeing your website as a true investment.
You protect your car by changing the oil, checking the tires and doing other maintenance on it, correct? You have insurance in case of an accident. You might even have home warranty to cover broken appliances.
Website owners pay content creators to write articles, they pay designers to create imagery to enhance their content, and they pay some more people to publish and promote their content on Social Media and Search Engines.
Very few own their own servers and even fewer employ full-time (or even part-time) administrators; and if they do, it’s usually to keep the internal systems (Windows, Office, etc) running. The website however – although the livelihood for some – gets treated like the proverbial red-headed step child, with required maintenance often grossly neglected or simply not done at all. It’s just expected to work.
Like I’ve said before, as a website owner, or the owner of an account with a hosting company, you are responsible for your website, its content and its security – especially if you’re conducting any kind of e-commerce!
Similar to installing a home security or monitoring system or a car alarm: Your website deserves protection as well.